Make Your Healthcare Software HIPAA Compliant
Healthcare is a billion dollar industry. Last decade is quite evident that a great deal of patient information has been compromised. This has directly impacted the credibility of health applications and the industry in question.
Therefore, to address constraints of Privacy, Security, Enforcement and Breach Notification, the Health Insurance Portability and Accountability Act aka HIPAA has laid regulations.
What is HIPAA Compliance?
HIPAA compliance involves fulfilling the requirements of the Health Insurance Portability and Accountability Act (HIPPA) of 1996, its subsequent amendments, and any related legislation such as the Health Information Technology for Economic and Clinical Health (HITECH) Act.
What does it mean to be in compliance with HIPAA?
HIPAA sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have the physical, network, and process security measures in place and follow them to ensure HIPAA Compliance.
The United States mandate their inclusion so that customers have access to a more viable app.

Case: Anthem, the leading US Insurance firm had to pay a heavy price
Theft of patient data can lead to heavy losses, fraud, blackmail and whatnot. US law mandates HIPAA in order to maintain the privacy of such crucial information. And the case that follows is an apt exemplification of what makes HIPAA essential in applications –
Anthem is the largest US Insurance firm. It offers its considerable health benefits and medical care to US citizens under their affiliated health policies. The company has witnessed the largest breach in US healthcare.
Cyber attackers targeted the company’s advanced IT systems causing an ePHI (electronic Patient Health Information) breach of nearly 79 million patients in a series of cyber attacks. Compromised information included SSN, addresses, names, employment information, email addresses, date of birth and medical identification number.
This advanced persistent threat attack had the sole purpose of extracting the information of patients thereby violating civil rights. Anthem had failed to meet the HIPAA guidelines which resulted in a legal obligation on the company from the client for no less than $115 M. Furthermore, the company had to spend nearly $260 M to ameliorate security measures.
Any organization, big or small, may face serious consequences if they ignore HIPAA regulations unless they are able to afford a crazy amount of money and compromise on their patients’ trust.
HIPAA to help healthcare Providers and Patients
Anthem could have easily avoided the situation by careful assessment of security systems and measures.
The law requires healthcare providers such as hospitals and Business Associates (3rd parties handling patients’ information) to fulfil the pre-requisites of HIPAA. The law also requires compliance even when the party has an indirect relation with PHI.
The compliance calls for regular assessment and audits for the security and privacy of healthcare information. The assessment encompasses Physical and Technical safeguards that HIPAA outlines.
- Technical safeguards – These ensure emergency access, encryption, login, past activities, etc.
- Physical safeguards – Protecting the system containing PHI such as PCs, data centres, servers, laptops, etc.
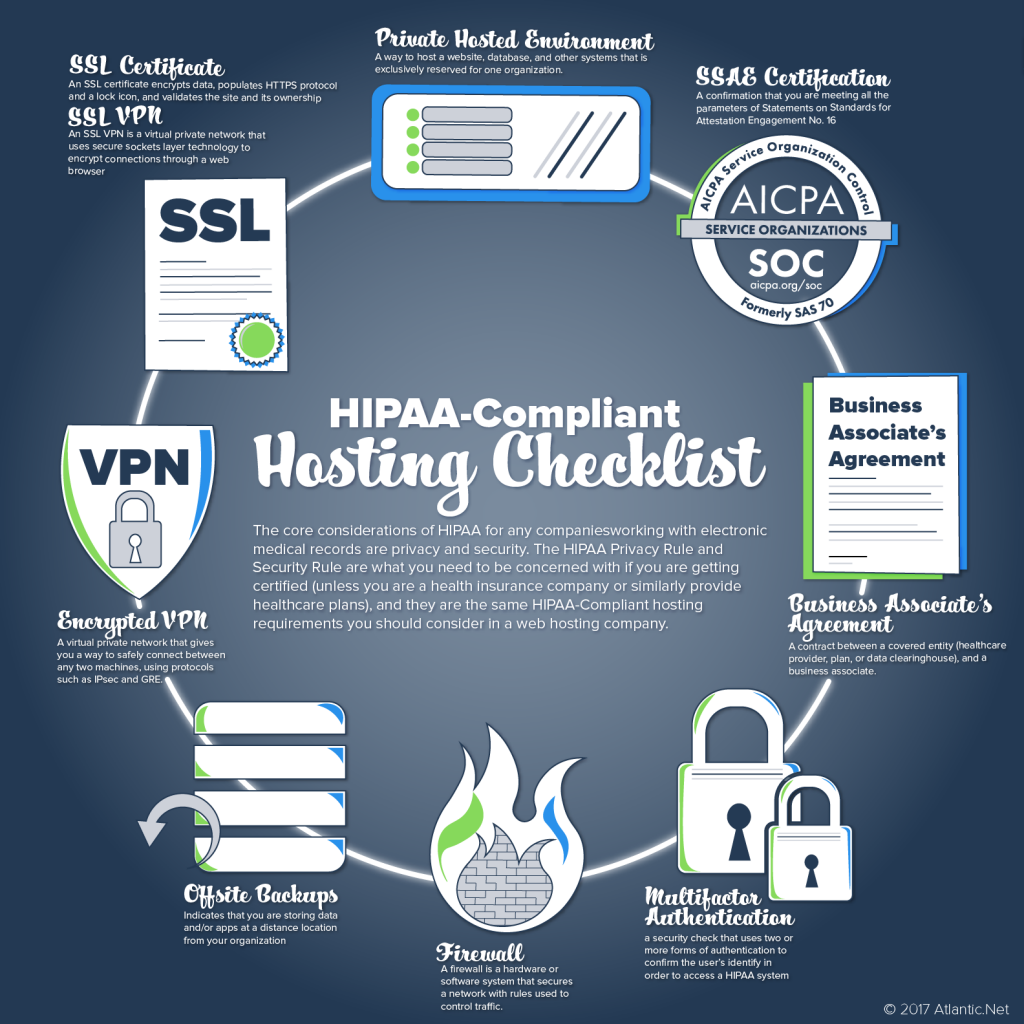
And a Features Checklist to verify your Hippa Compliant Healthcare application
| Features | Details |
| Secure Transmission | Patients’ data shared over a network needs the utmost security. |
| Access Control | This feature mandates authorizing access to PHI. HIPAA states no person should have access to information they are not allowed to. Even the patients can get to decide who should or should not have access to his/her PHI. |
| Authenticating entity | Every user trying to gain access to Patients’ data should present his/her identification. It is possible through the implementation of Password, Biometrics, physical identification, and PIN (Personal Identification Number). |
| Backup | To maintain the integrity factor in patient’s data, it is quintessential to keep PHI in copies. |
| Monitor the activity on PHI | PHI is prone to use by personnel of all levels. It is important to monitor any fixes, modifications, deletions or access to the data that is susceptible to attack. |
| Disposing of Safely | Healthcare providers or Business Associates should define clear methods for successful disposal of PHI when it is no longer required. In addition to PHI, health care providers should also destroy the source of PHI such as pen drives or floppy disks. |
| Encrypt the data | One of the proven ways to ensure PHI security is to encrypt it before transmission so that the recipient can only decrypt it with a key. |
| Activity Logs and Audit Controls | The audit controls required under the technical safeguards are there to register attempted access to ePHI and record what is done with that data once it has been accessed. |
| Mobility of Devices | Protection of mobile devices is imperative as they are easily lost or misused. Measures such as locking, encrypting, or remotely deleting the data need encouragement among healthcare providers. |
Let Wildnet Technologies develop a HIPAA compliant Healthcare Application for you
Wildnet’s team of Expert Web, Mobile Apps and Salesforce Cloud CRM Developers have wealth of experience in producing best-in-class healthcare applications. Undoubtedly, these applications fulfil one and only pre-requisite – HIPAA compliance.
As the law of the United States mandates HIPAA for PHI security and integrity, it is quintessential for all Software Developers to efficiently meet HIPAA guidelines. And that is exactly what we do! We design healthcare applications bearing in mind the importance of end-user data.
Do you have an application in mind? Write to us!
Need help ! Contact Us