It’s as safe as amazing it is
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most democratic free security tools. It helps you to find security vulnerabilities in your web applications automatically while developing and testing the applications.
ZAP is an amazing tool for experienced pen testers for manual security testing. It’s an easy to use integrated penetration testing tool for sorting vulnerabilities in web applications.
Designed in such a way to be used by people with a wide range of security experience & as such is ideal for developers and functional testers who might be penetration testing.
Threats Monitored:-
Top 10 threat attacks are catered by ZAP tool are
A1 – Injection: –
Injection a flaw, such as SQL, OS, and LDAP injection happens when over trusted data is passed to an interpreter as part of a command or query. The attacker’s hostile data can trap the interpreter into processing unintended commands and accessing data without actual authorization
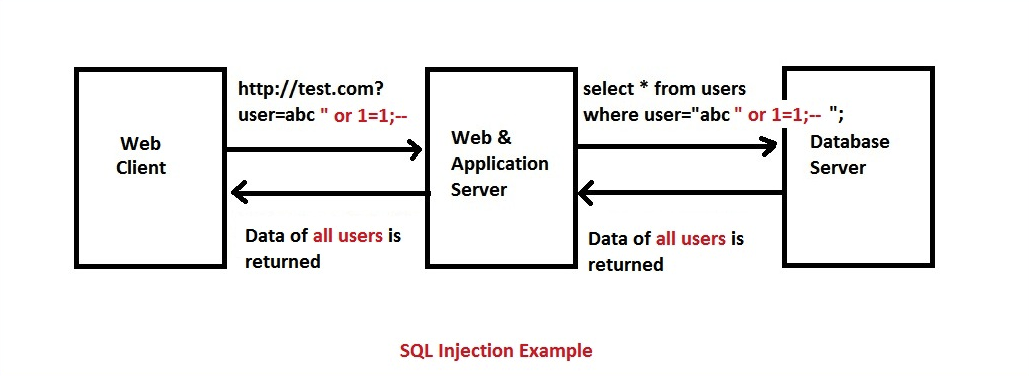
A2 – Broken Authentication and Session Management –
Application functionality related to authentication and session management is often not applied correctly, allowing attackers to compromise passwords, session tokens or keys, and also to exploit other implementation flaws just to assume other users’ identities.

A3 – Cross-Site Scripting (XSS) –
XSS flaws occur at the time any application takes untrusted data and passes it to a web browser without actual validation or escaping. XSS allows attackers to carry out scripts in the victim’s browser which can hijack user sessions, redirect the user to malicious sites or deface web sites.
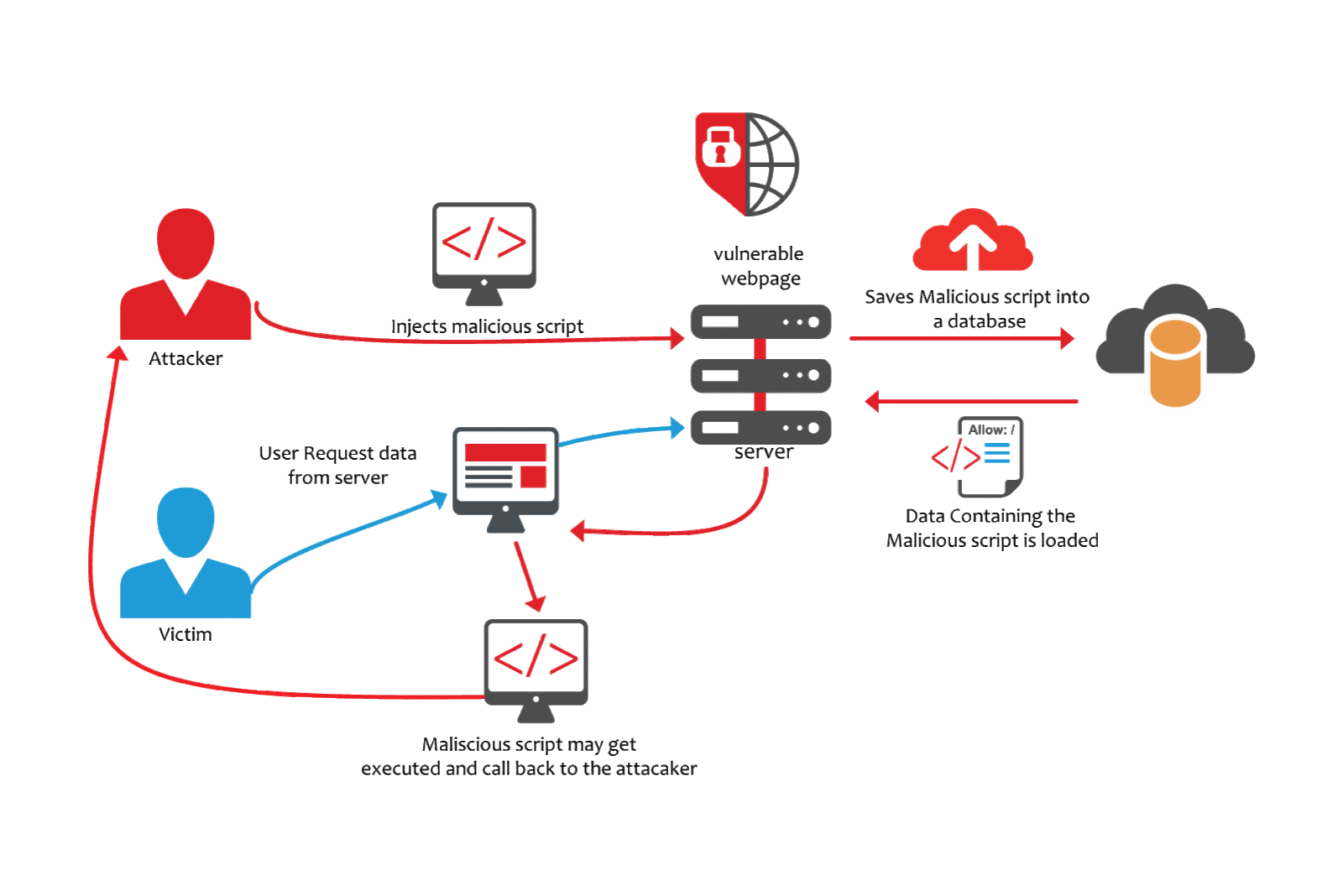
A4 – Insecure Direct Object References –
A direct object reference take place when a developer exposes a reference to an internal implementation object, like a file, database key, or directory. Lack of any access control check or any other protection, attackers can easily manipulate these references to access unauthorized data.
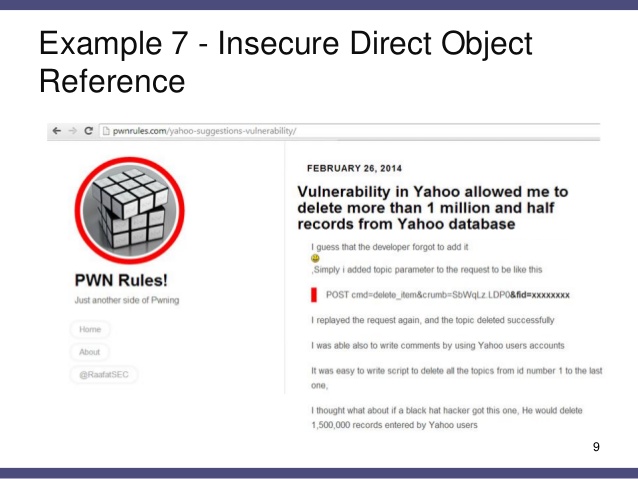
A5 – Security Misconfiguration –
Effective security requires having a secure configuration definite and deployed for the application, application server, frameworks, web server, and database server platform. Secure settings must be defined, implemented, and maintained, as defaults are often insecure and, software should be up to date.
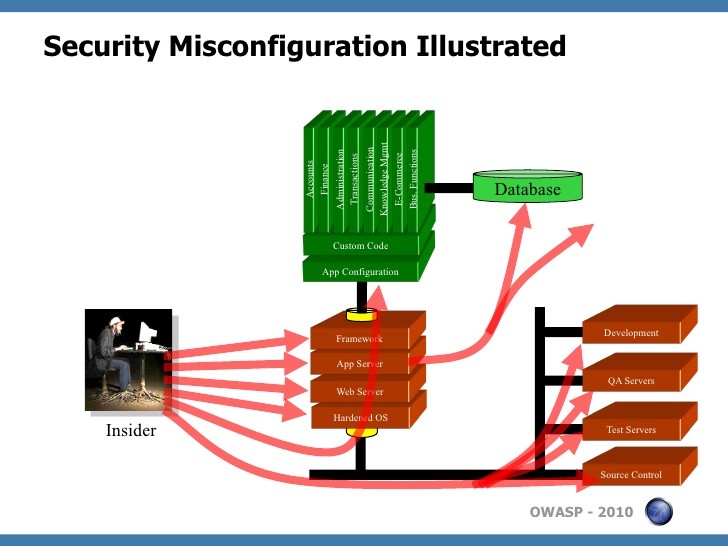
A6 – Sensitive Data Exposure –
Various web applications do not effectively protect sensitive data, like credit cards; authentication credentials and tax IDs. Attackers might steal or tweak such weakly protected data to execute credit card fraud, identity theft, or any other crimes. Sensitive data requires extra protection such as encryption at rest or in transit; also special precautions while exchanged with the browser.
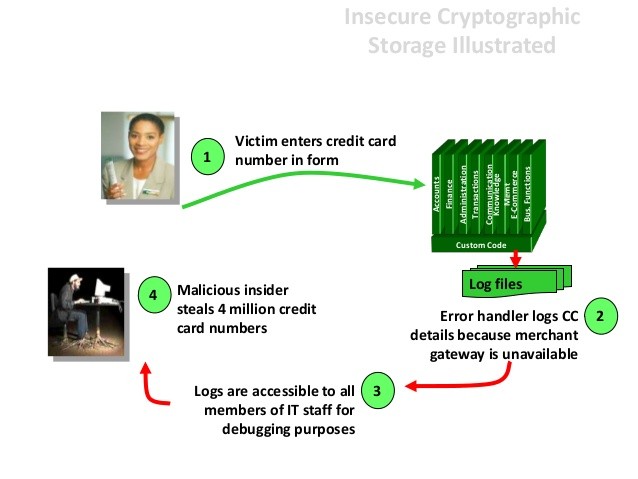
A7 – Missing Function Level Access Control –
Major web applications verify function level access just before making that functionality visible in the UI. But then, applications need to operate the same access control checks on the server while every function is accessed. In case requests are not verified, attackers will be able to formulate requests in order to access functionality without actual authorization.
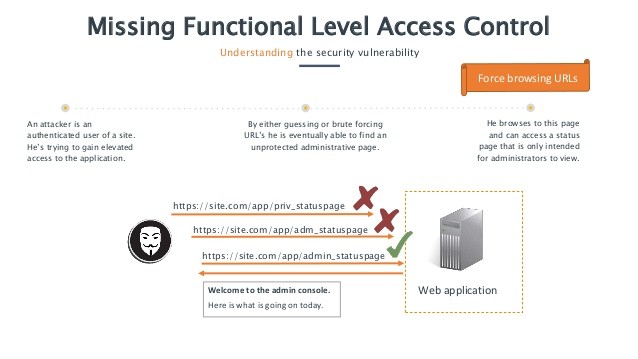
A8 – Cross-Site Request Forgery (CSRF) –
A CSRF attack insists a logged-on victim’s browser to send a false HTTP request, inclusive of the victim’s session cookie & any other automatically included authentication information, to a comprising web application. This allows the attacker to emphasize the victim’s browser for generating access or requests the vulnerable application thinks are legitimate requests from the victim.
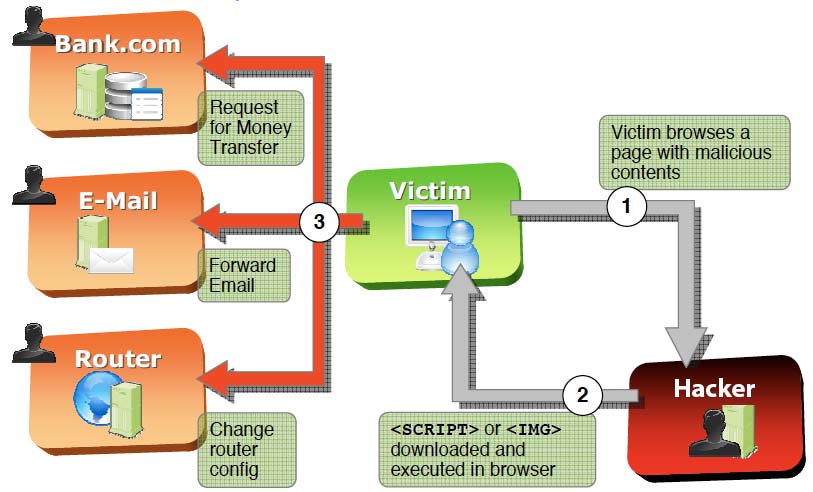
A9 – Using Components with Known Vulnerabilities –
Components, as libraries, frameworks, and other software modules, majorly always run with full privileges. In case a vulnerable component is exploited, such an attack can fetch serious data loss or server takeover. Apps using components with favorable vulnerabilities may undermine application defenses & enable a range of possible impacts and attacks.
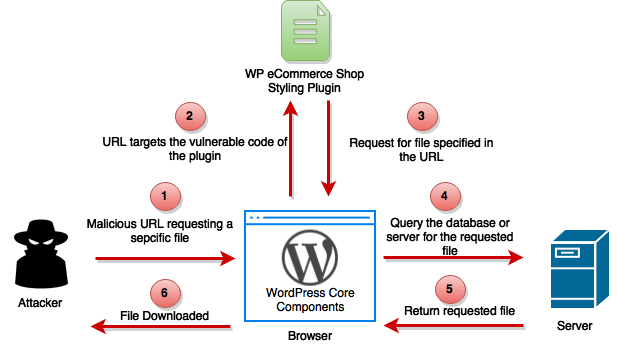
A10 – Unvalidated Redirects and Forwards –
Web applications frequently redirect and send users to other pages and websites, & use untrusted data for determining the destination pages. With no proper validation, attackers are able to redirect victims to phishing or malware sites, and also can use forwards to access unauthorized pages.

It’s crystal clear that learning & getting equipped with this tool is definitely gonna secure from major vulnerable that too rapidly. Relief is observing reduced threats in our web applications. Agreed?
Read More






